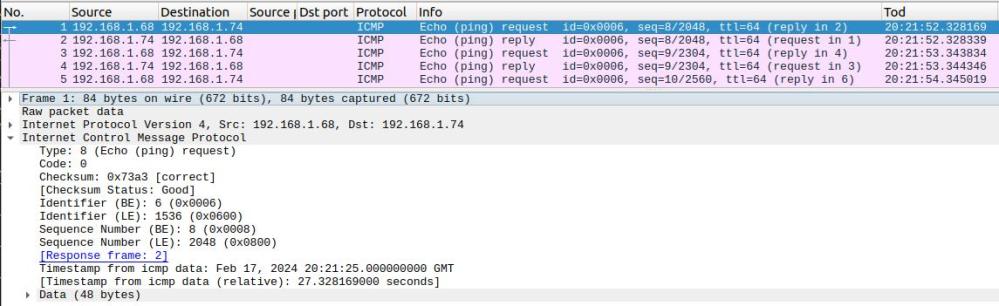
For example, a ping to z/OS as seen by z/OS
The TCPTRACE module runs as a batch job. It uses a documented TCPIP interface to collect packet trace data. It writes the trace data to a file which can be downloaded and used as input to wireshark.
Using the TCPTRACE module, you submit the job, run your test. Stop the job, download the file. Simple.
The documented way to collect a trace from z/OS is
- Start a CTRACE trace writer
- Start CTRACE
- Start TCP trace
- Run your test
- Stop TCP trace
- Stop Ctrace
- Stop Trace writer
- use IPCS to process the trace and create a file to download
- Download the file
Which is complex and has many steps.
Ive created a github project called zWireshark. You only need the load module, the source is there for example.
Please let me know of any suggestions or improvements.
Let me see if I have this straight. TCPTRACE is a replacement for (when doing a TCP/IP trace), CTRACE, GTF and IPCS? None of those have to be run; only TCPTRACE?
LikeLike
yes – it is that simple- and the program is pretty simple about 1K of c!
LikeLike
Wow. Seems like IBM should have done this long ago!
LikeLike
Hello Colin. This sounds great. I downloaded a copy of the program, APF authorized it and also created the RACF profile in SERVAUTH class and granted myself READ access, however i am getting a 0C4 reason 4 abend. Inaccessible storage
Regards,
Daniel
LikeLike
Daniel,
Thanks for letting me know.. Could you paste the error info – such as where it failed!
thank you
Colin
LikeLike
Hi Daniel,
It has abended in old code. Meaning that the value passed in was a bad pointer.
Did you get any other output?
Would you be happy sending me the CEEDUMP? colinpaicemq@gmail.com
If not please try adding –DEBUG 1 and send me the output… so I can see if you had any errors from the calls.
You should have output like
Using port: 0
payload length: 1024
>20:09:28.710920 Src 10.1.0.2 Port 0 –Dst 7.168.1.74 Port 0
00000000 : 45000054 4E444000 3F01DA70 0A010002 ….+. ……… E..TND@.?..p….
00000010 : 07A8014A 08009B72 000A0001 DDA9D765 .y………..zP. …J…r…….e
00000020 : 00000000 DE9F0A00 00000000 10111213 ……………. …………….
00000030 : 14151617 18191A1B 1C1D1E1F 20212223 ……………. ………… !”#
00000040 : 24252627 28292A2B 2C2D2E2F 30313233 ……………. ¢%&'()*+,-./0123
00000050 : 34353637 …. 4567
LikeLike
Hi Colin, please find error below.
CEE3204S The system detected a protection exception (System Completion Code=0C4).
From compile unit S0W1://’COLIN.C.ZWIRESHA(PRINTHX)’ at entry point printHex at statement 58 at compile unit offset +000000002DA008CC at entry offset +000000000000015C at address 000000002DA008CC.
Regards,
Daniel
LikeLike
Hi Daniel,
I think I have fixed the problem in printhex. I was using the wrong length. As part of fixing it, I’ve also simplified the logic. Please let me know if the new version works.
LikeLike